We live in a world where cyber-crime is becoming a major threat and the level and sophistication of the exploits being issued by hackers has increased considerably recently. Hackers realise that they can very easily coerce users into clicking on dodgy links in phishing emails and then run virus or malware on users’ computers. Users being lulled into clicking on seemingly genuine links in emails is a typical way for a virus or malware to be enacted.
There is an increasing trend towards ransomware being the payload of choice for cyber criminals as this is something that can be easily monetised. Ransomware encrypts a user’s personal files and will only release them back to the user if a ransom is paid – usually using the anonymous digital currency Bitcoin.
WannaCry attack
WannaCry is a typical example of ransomware, but with a twist that enables it to quickly spread across an organisation’s computers making it a very dangerous threat.
On 12 May 2017 a massive ransomware attack was launched across the world. The target seemed to be a random mix of household names, but the highest profile victim appeared to be the UK’s National Health Service.
By lunchtime, reports were coming into us of several NHS trusts being wiped out by this attack and IT security teams were scrambling around to find out the cause and how to defeat the problem. At this stage, we were pleased that we had not already been infected and had to act quickly to ensure this continued.
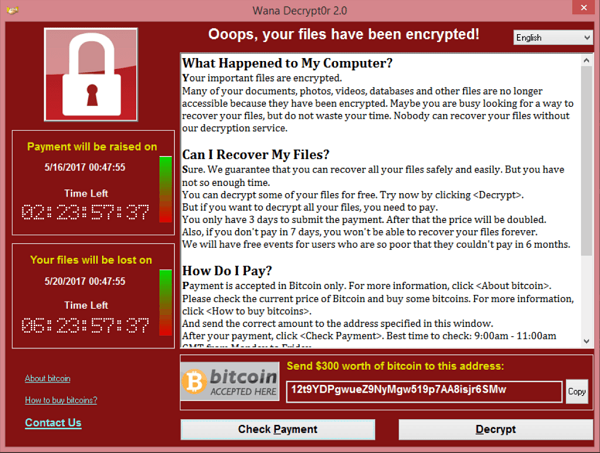
Resisting the attack
Our first line of defence is always education for our users. For some time we’ve tried to raise awareness with staffon how to notice suspicious phishing emails and report them to us. There is a fairly good understanding of these issues from most users but the degree of thought and effort going into the wording of many of these phishing emails is improving all of the time. With WannaCry it would only take a single user to potentially infect every other computer and server on our network so it was critical that we acted fast.
Our second line of defence is our anti-virus software, which is installed to all computers and servers on our network. We employ several different brands of antivirus to improve our protection. Our standard procedure is for the latest anti-virus definition file updates to be issued several times a day to users in the background and according to our monitoring system we had a high level of coverage for the latest updates without any specific manual intervention.
If the anti-virus software is working it should protect a computer from initially getting infected by the ransomware so in most cases WannaCry would be prevented from downloading and running.
The part about WannaCry that made it so dangerous is that the damage that it could do was not just limited to encrypting files on a user’s computer. A security vulnerability discovered in March 2017 in Microsoft’s SMB protocol (used for file sharing across networks) meant that WannaCry could leapfrog onto any other computer or server that it could see. This would potentially have a catastrophic effect and every computer in an organisation could be taken out within seconds.
Our third line of defence is ensuring that security patches and operating system updates on computers and servers are up to date. Microsoft had recently released security patch MS017 that specifically fixed the flaw in Windows which WannaCry exploits to propagate across computers on a network. (Microsoft released this security patch for all supported versions of Windows but this did not initially include Windows XP and Server 2003 as these are considered ‘unsupported’ operating systems.)
Our monitoring systems suggested that a relatively high percentage of our computers were protected against this vulnerability but we quickly put in place a process of re-sending this MS17 security update to all computers that were connected to our network.
By mid-afternoon the SMB security vulnerability was confirmed as the key element that needed to be plugged and advice was issued to remotely disable SMB and patch computers as soon as possible.
We quickly discussed what we should do and our various options. Even though the recommendation was to disable SMB protocol we felt this would potentially have an unknown effect on file sharing and how systems share files between each other, potentially having mulyiple knock-on effects. Our various IT systems share data between them and we didn’t have a clear picture of what the effect of disabling SMB would be.
Internet and email temporarily restricted as a precaution
We decided to immediately disable internet access for all users which should prevent any initial infection by restricting access to download WannaCry. We also decided to quarantine any emails that came into our email servers that contained website links or attached documents – again preventing staff from clicking on the WannaCry links. This would ensure that any potentially infectious emails would not get through and give us time to improve our deployment of the MS17 security patch to ensure as close to 100% coverage as possible.
We kept the internet and email restrictions in place over the weekend as a precautionary measure whilst the few outstanding critical servers were patched. We restored a “whitelist” internet on Monday morning, which allowed users to access business critical websites, but continued to restrict everything else. By Monday evening we felt comfortable to restore internet and deliver the thousands of emails that had been quarantined.
It became clear over the following week that the NHS hadn’t been target specifically, but that organisations with a weak approach to IT security looked to be hit hardest. Those organisations operating Windows XP were very susceptible to this problem as Microsoft had not issue a security patch for this initially (although it later did due to the scale of the issue).
Cyber security is something we take very seriously. We ensure that all of our computers are protected against malicious attacks as best we can. We also ensure that security is high on our agenda with the new digital systems that we are building to ensure that our users can have a high level of trust and assurance with using our services online.

